Yoursites123 is a browser hijacker that modifies your web browser and Windows registry. It's very similar to
Mysearch123. Once installed, it will change your home page and default search engine provider to Yoursites123 (http://www.yoursites123.com/). It's not a real search engine, even though it may look like the real thing. It simply redirects your searches to globososo.inspsearch.com or similar websites that most likely pay for search traffic. Inspsearch.com is not a new kid on the block. I mentioned in my previous article about
Delta-homes browser hijacker. Despite being blocked by most antivirus engines it still manages to operate successfully and generate revenue which is without a doubt the main reason why browser hijackers are creates in the first place. When it comes to browser hijackers, we are talking about something that can have an annoying – and sometimes dangerous – effect on your computer.
Browser hijackers are characterized by the fact that they come in the guise of something that appears to be innocent – and often useful. They magically manifest themselves as a tool bar, a home page, a browser or a search engine. In this case Yoursites123 is installed as a homepage or a startup page is you want. At this point you could be forgiven for thinking 'but what is so wrong with that?' After all, these are things that we depend on daily when we are using our computers or tablets.
The Yoursites123 problem The issue with browser hijackers is that they install themselves on your desktop, laptop or tablet without expressly asking your permission. The silver lining to the cloud is that most browser hijackers are not especially dangerous – but nevertheless they take it up a notch on the annoyance scales and can leave you tearing your hair out in frustration as you battle with them. Just like their furry counterparts, these browser hijackers are extremely willful and will do exactly what they want.
That might not involve pooping on the rug, but they will replace your existing functions with their own versions. These will then redirect your internet searches to websites that the Yoursites123's programmer wants you to visit. They can also have a serious effect on your PC's security posture – due to this redirecting of your searches to unknown, and often dubious, websites.
How did I end up with the Yoursites123 on my PC?In the majority of cases, Yoursites 123 will come neatly bundled with another program – and that could be anything from an upgrade to your trusted online VoIP app or a free game that a friend or acquaintance sent you in a link via an email or chat message. However, one thing to bear in mind is that it doesn't matter what you are downloading – browser hijackers aren't fussy and will hitch a ride with anything from a reputable PDF viewer to sparkly wallpaper or emoji downloads.
The good news is that YOU have a choice in whether you install a browser hijacker or not. This means that they are normally mentioned in the original download's End User License Agreement (EULA). A browser hijacker programmer will claim that their annoying, redirecting, mischievous browser hijacker is just as potentially wanted as it is unwanted – meaning they do not have anything to be surreptitious about.
How to avoid a browser hijackerYou've probably already come to the conclusion that if you don't want Yoursites123 on your computer, the best course of action you can take is to read the EULA properly!
How do I remove Yoursites123?It can be a tedious task. It modifies browser settings and also makes modifications to Windows registry. Hopefully, the removal guide below will help you to remove this browser hijacker from your computer. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by
Michael Kaur, http://deletemalware.blogspot.com
Yoursites123 Removal Guide:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this infection. Hopefully you won't have to do that.
2. Remove Yoursites123 related programs from your computer using the
Uninstall a program control panel (Windows 7). Go to the
Start Menu. Select
Control Panel →
Uninstall a Program.
If you are using Windows 8 or 10, simply drag your mouse pointer to the right edge of the screen, select
Search from the list and search for "control panel".

Or you can right-click on a bottom left hot corner (formerly known as the Start button) and select
Control panel from there.

3. When the
Add/Remove Programs or the
Uninstall a Program screen is displayed, scroll through the list of currently installed programs and remove the following programs:
- Yoursites123
- LiveLyrics
- GoSave
- ExtTag

If you are using Windows Vista, Windows 7 or Windows 8, click
Uninstall up near the top of that window. When you're done, please close the Control Panel screen.
Remove Yoursites123 from Google Chrome:1. Click on
Chrome menu button. Go to
More Tools →
Extensions.
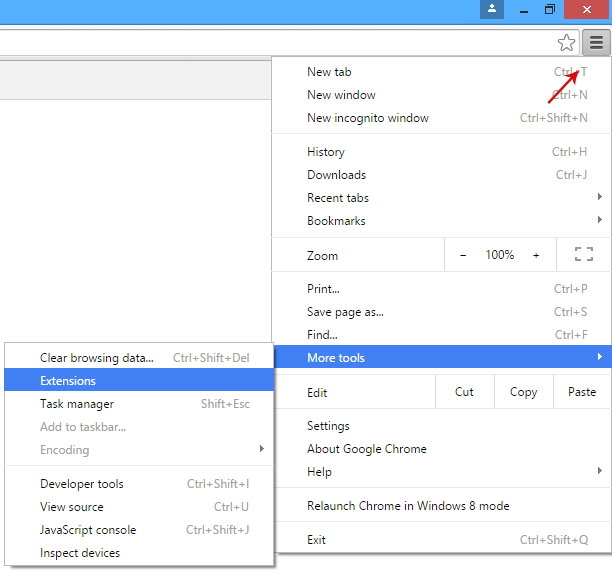
2. Click on the
trashcan icon to remove Yoursites123, PursuePoint, LiveLyrics, GoSave, ExtTag, BookmarkTube extensions.
3. Then select
Settings. Scroll down the page and click
Show advanced settings.

4. Find the
Reset browser settings section and click
Reset browser settings button.

5. In the dialog that appears, click
Reset.
6.
Right-click Google Chrome
shortcut you are using to open your web browser and select
Properties.
7. Select
Shortcut tab and remove "http://www.yoursites123.com/..." from the Target field and click OK to save changes. There should be only the path to Chrome executable file.
Remove Yoursites123 from Mozilla Firefox:1. Open Mozilla Firefox. Go to
Tools →
Add-ons.
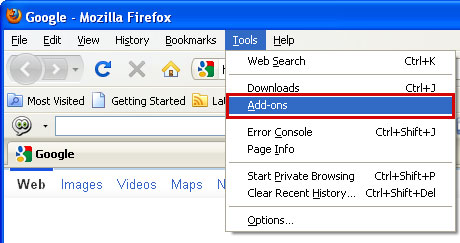
2. Select
Extensions. Remove Yoursites123, PursuePoint, LiveLyrics, GoSave, ExtTag, BookmarkTube browser extensions. Close Add-ons manger.
3. In the URL address bar, type
about:config and hit Enter.

Click
I'll be careful, I promise! to continue.

In the search filter at the top, type:
yoursites123Now, you should see all the preferences that were changed by yoursites123.com. Right-click on the preference and select
Reset to restore default value.
Reset all found preferences!4.
Right-click the Mozilla Firefox
shortcut you are using to open your web browser and select
Properties.
5. Select
Shortcut tab and remove "http://www.yoursites123.com/..." from the Target field and click OK to save changes. There should be only the path to Firefox executable file.
Remove Yoursites123 from Internet Explorer:1. Open Internet Explorer. Go to
Tools →
Manage Add-ons.
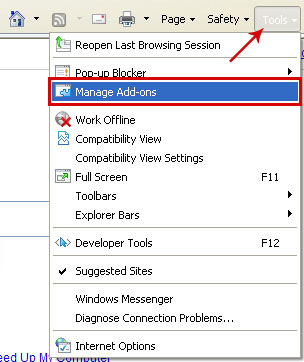
2. Select
Search Providers. First of all, choose
Live Search search engine and make it your default web search provider (
Set as default).
3. Select
yoursites123.com and click
Remove to remove it. Close the window.
4.
Right-click the Internet Explorer
shortcut you are using to open your web browser and select
Properties.
5. Select
Shortcut tab and remove "http://www.yoursites123.com/..." from the Target field and click OK to save changes. Basically, there should be only the path to Internet Explorer executable file.

 BluePink
BluePink  BluePink
BluePink